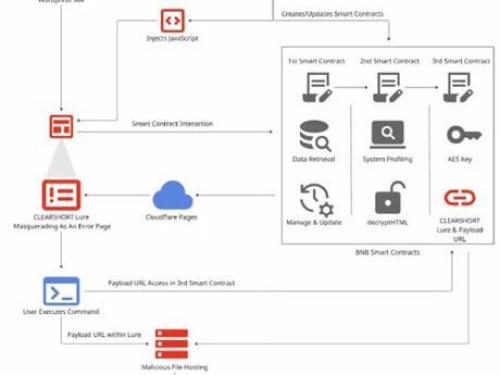
Blockchain's immutability is weaponized: Learn about "EtherHiding," where UNC5142 hosts malware on BNB Smart Chain smart contracts. Discover why traditional security fails and how to secure decentralized networks.
A Sybil attack lets one adversary create countless fake identities, distorting market signals & faking liquidity on DEXs. Learn how this threat enables wash trading, governance takeover, and price manipulation, and discover defense-in-depth strategies.
A double-spending attack is when a fraudster tries to spend the same cryptocurrency twice by manipulating the blockchain. 🌐💰 The scammer first makes a transaction and then tries to erase the record of that transaction from the ledger.