How is crypto tracked? Learn how the FBI, DHS, Chainalysis, and Elliptic monitor transactions through exchanges. Full tracking schemes revealed. Read more!
Why SMS 2FA is a security relic. Learn why SIM swapping makes SMS codes useless and how the TOTP standard (RFC 6238) provides real account protection.
The ultimate guide to Zero-Knowledge Proofs (ZKPs): See how Zcash, Firo, and Aleo hide sender, receiver, and amount. SNARKs vs. STARKs explained for blockchain privacy.
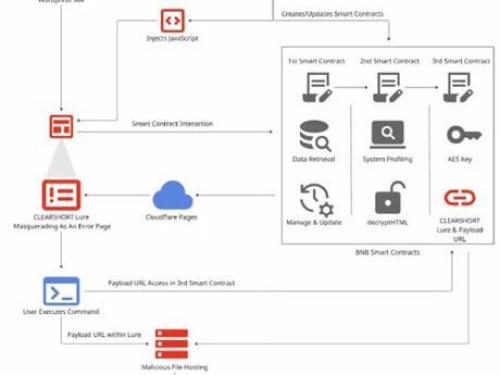
Blockchain's immutability is weaponized: Learn about "EtherHiding," where UNC5142 hosts malware on BNB Smart Chain smart contracts. Discover why traditional security fails and how to secure decentralized networks.
A Sybil attack lets one adversary create countless fake identities, distorting market signals & faking liquidity on DEXs. Learn how this threat enables wash trading, governance takeover, and price manipulation, and discover defense-in-depth strategies.
Secure your digital life! Get the definitive setup guide for end-to-end encrypted messaging using Jabber (XMPP), SSL/TLS, and GPG (GnuPG). Learn to integrate the Psi client, generate keys, and protect your communications from leaks. Master secure messaging now!
Short and actionable - how and why to create multiple privacy profiles on an exchange to split risk, reduce correlation, and keep your digital life both secure and manageable.