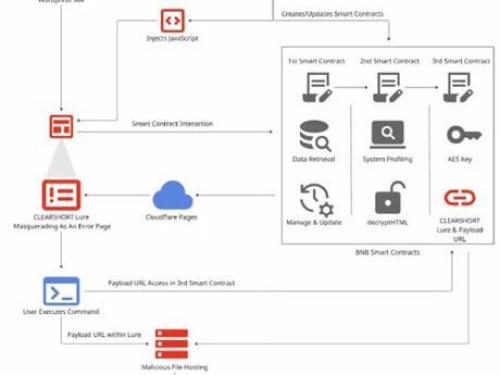
Blockchain's immutability is weaponized: Learn about "EtherHiding," where UNC5142 hosts malware on BNB Smart Chain smart contracts. Discover why traditional security fails and how to secure decentralized networks.
A Sybil attack lets one adversary create countless fake identities, distorting market signals & faking liquidity on DEXs. Learn how this threat enables wash trading, governance takeover, and price manipulation, and discover defense-in-depth strategies.
Even the largest, most regulated crypto exchanges with billions in trading volume have fallen to hackers. What the history of exchange hacks really teaches us is simple: security isn’t about paperwork — it’s about infrastructure. Anonymous, privacy-first platforms like EXMON that avoid storing personal data often turn out to be far more resilient in the real world.
A 51% attack is one of the scariest threats to blockchain networks, with the potential to disrupt their integrity and security. In this article, we’ll break down what a 51% attack is, how it works, and look at real-life examples with Bitcoin Gold and Ethereum Classic.