The blockchain industry has spent over a decade positioning itself as the foundation of digital trust — decentralized, transparent, and immutable. But that same immutability can turn into a weapon when leveraged by threat actors.
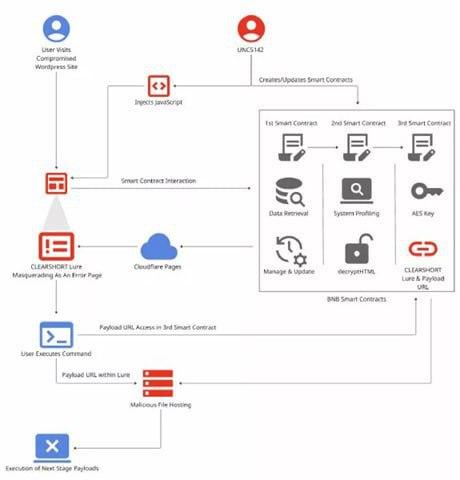
Recently, Mandiant Threat Defense and Google Threat Intelligence exposed a campaign by UNC5142, a threat group using BNB Smart Chain smart contracts to host and distribute malware. This new attack vector, dubbed “EtherHiding,” marks a significant shift in how malicious actors are exploiting decentralized infrastructures.
How the Attack Works
The campaign unfolds in several stages:
- Initial Compromise: Attackers breach vulnerable WordPress sites.
- Payload Delivery: Injected scripts connect to malicious BNB Smart Chain contracts.
- Execution: These contracts deliver malware (typically info stealers) directly from the blockchain to victims’ systems.
Since the payload is stored on-chain, it’s immutable — you can’t simply “takedown” a smart contract the way you would a malicious domain or server. Once deployed, it’s there permanently.
Why It Works
1. Low Cost of Entry
Deploying a smart contract on BNB Smart Chain can cost less than $0.25, making it trivial for attackers to scale distribution.
2. Decentralization as a Shield
Decentralized networks offer resilience and censorship resistance — the same properties that make it almost impossible to remove malicious code.
3. Cross-Chain Portability
The concept isn’t limited to BNB. The same technique can easily migrate to Ethereum, Polygon, or Solana, where smart contracts and dApps are just as accessible.
Implications for the Industry
This is more than just another campaign — it’s a proof of concept that shows how public blockchains can serve as malware delivery platforms.
It forces us to ask critical questions:
- How do we monitor and respond to malicious activity inside decentralized networks?
- Should blockchain explorers and RPC providers begin scanning for suspicious contract patterns?
- How can exchanges, wallets, and dApps ensure their frontends and APIs aren’t unknowingly interacting with malicious contracts?
The traditional security stack — firewalls, domain blacklists, IP reputation — doesn’t apply here. On-chain data lives forever, and once malware is encoded in a smart contract, it becomes part of the ledger itself.
The Way Forward
The crypto ecosystem needs to start treating blockchains as part of the attack surface.
That means:
- Integrating on-chain threat intelligence into SOC pipelines.
- Building heuristics to identify abnormal contract behavior.
- Coordinating with major chain operators and RPC providers to flag malicious deployments.
At our exchange, we’re already expanding our internal monitoring tools to include on-chain anomaly detection — scanning for malicious payloads and interactions tied to our ecosystem.
The line between “smart contract” and “malware host” is blurring fast.
Final Thoughts
Blockchain technology was built on the idea of trustless infrastructure, but trustless doesn’t mean harmless.
As the boundary between cybersecurity and decentralized systems disappears, it’s on the industry to evolve faster than the threat actors do.
The future of blockchain security isn’t just about protecting assets — it’s about securing the chains themselves.